Cyber Security Training
Master cyber defense skills with hands-on projects using real-world security scenarios
- Learn essential tools: Kali Linux, Wireshark, Python, Firewall Configuration, SIEM Tools, and Networking
- Live online and offline interactive sessions led by top industry security experts
- Guaranteed placement support through our career advancement services
- Understand ethical hacking, penetration testing, network security, threat detection, and incident response

World-Class Instructors

1:1 with Industry Mentors
55% Avg. Salary Hike

Interview Preparation

World-Class Instructors

1:1 with Industry Mentors

55% Avg. Salary Hike

Interview Preparation
What You’ll Learn
Accelerate your career in cyber security with our Cyber Security Training at TechPragna in Bangalore. This comprehensive course equips you with the skills and techniques to protect digital assets, identify vulnerabilities, and mitigate cyber threats—perfect for both beginners and working professionals.
Cyber Security Training – Key Features
- Master Essential Tools: Kali Linux, Wireshark, Python, Metasploit, Burp Suite, and SIEM tools
- Learn Core Concepts: Ethical hacking, penetration testing, network security, and threat detection
- Hands-On Projects: Work on real-world cyber security scenarios and practical simulations
- Live Interactive Sessions: Attend online and offline sessions led by top industry professionals
- Career Advancement Support: Receive guaranteed placement assistance with interview preparation
- Beginner-Friendly Approach: Suitable for freshers, IT professionals, and career switchers
Request more information
What You’ll Learn
Accelerate your career in cyber security with our Cyber Security Training at TechPragna in Bangalore. This comprehensive course equips you with the skills and techniques to protect digital assets, identify vulnerabilities, and mitigate cyber threats—perfect for both beginners and working professionals.
Cyber Security Training – Key Features
- Master Essential Tools: Kali Linux, Wireshark, Python, Metasploit, Burp Suite, and SIEM tools
- Learn Core Concepts: Ethical hacking, penetration testing, network security, and threat detection
- Hands-On Projects: Work on real-world cyber security scenarios and practical simulations
- Live Interactive Sessions: Attend online and offline sessions led by top industry professionals
- Career Advancement Support: Receive guaranteed placement assistance with interview preparation
- Beginner-Friendly Approach: Suitable for freshers, IT professionals, and career switchers
Request more information
Cyber Security Course Curriculum
Introduction to Cybersecurity
What is Cybersecurity and Why It Matters
Common Cyber Threats (Malware, Phishing, DDoS)
CIA Triad: Confidentiality, Integrity, Availability
Cybersecurity Roles (Analyst, Engineer, SOC)
Cybersecurity Frameworks (NIST, ISO 27001)
Real-World Cyberattack Case Studies
Career Paths and Certifications (CISSP, CEH, Security+)
Essential Tools Overview (Wireshark, Metasploit, SIEMs)
Networking Fundamentals for Security
TCP/IP Model and Key Protocols (HTTP, DNS, SSH)
Network Topologies and Attack Surfaces
Firewalls, IDS/IPS Systems
VPNs and Secure Remote Access
Wireless Security (WPA3, Evil Twin Attacks)
Network Scanning with Nmap
Packet Analysis with Wireshark
Lab: Simulating Network Attacks/Defenses
Operating System Security
Hardening Windows/Linux Systems
User Authentication (MFA, Biometrics)
Patch Management and Vulnerability Mitigation
File System Permissions and Encryption
Logging and Auditing (SIEM Integration)
Virtualization Security (Hypervisor Risks)
Endpoint Protection (EDR, Antivirus)
Lab: Securing an OS Against Exploits
Cryptography & Secure Communications
Encryption Basics (AES, RSA, ECC)
Hashing Algorithms (SHA-256, MD5)
Digital Signatures and PKI
SSL/TLS and HTTPS Implementation
Cryptographic Attacks (Collision, Side-Channel)
Secure Email (PGP, S/MIME)
Blockchain Security Fundamentals
Hands-on: Encrypting Data and Breaking Weak Ciphers
Threat Intelligence & Vulnerability Management
Types of Threat Actors (Hacktivists, APTs)
Vulnerability Assessment Tools (Nessus, OpenVAS)
Penetration Testing Phases (Recon to Reporting)
OWASP Top 10 Web Vulnerabilities
Zero-Day Exploits and Mitigations
Risk Assessment Frameworks (FAIR, OCTAVE)
Threat Hunting Techniques
Lab: Conducting a Vulnerability Scan
Ethical Hacking & Pen Testing
- Kali Linux Tools (Metasploit, Burp Suite)
- Social Engineering (Phishing, Pretexting)
- Exploiting Web Apps (SQLi, XSS, CSRF)
- Network Exploitation (MITM, ARP Spoofing)
- Privilege Escalation (Windows/Linux)
- Post-Exploitation (Pivoting, Data Exfiltration)
- Legal and Compliance (PenTest Licensing)
- Capture-the-Flag (CTF) Challenges
Incident Response & Digital Forensics
Incident Response Lifecycle (NIST SP 800-61)
Forensic Tools (FTK, Autopsy, Volatility)
Evidence Acquisition and Chain of Custody
Malware Analysis (Static/Dynamic)
Log Analysis (SIEM Queries)
Ransomware Response Strategies
Disaster Recovery Planning
Simulated Cyberattack Response Drill
Cloud & IoT Security
Shared Responsibility Model (AWS/Azure/GCP)
Securing Cloud Storage (S3 Buckets, IAM Policies)
Container Security (Docker, Kubernetes)
IoT Attack Vectors (Botnets, Firmware Hacks)
Cloud-Specific Threats (Misconfigurations, API Abuse)
DevSecOps Integration
Case Study: Cloud Breaches (Capital One, SolarWinds)
Lab: Securing a Cloud Deployment
Identity & Access Management (IAM)
Authentication vs. Authorization
Role-Based Access Control (RBAC)
Single Sign-On (SSO) and SAML
Passwordless Authentication (FIDO2)
Privileged Access Management (PAM)
Active Directory Security
IAM for Cloud Environments
Lab: Implementing MFA and Access Policies
Security Compliance & Governance
GDPR, HIPAA, PCI-DSS Overview
Security Policies and Procedures
Auditing and Compliance Checklists
Third-Party Risk Management
Business Continuity Planning (BCP)
GRC (Governance, Risk, Compliance) Tools
Case Study: GDPR Fines and Enforcement
Workshop: Drafting a Security Policy
Advanced Topics (Choose Focus Areas)
- AI in Cybersecurity (Threat Detection)
- OT/ICS Security (SCADA Systems)
- Red Team/Blue Team Exercises
- Bug Bounty Programs
- Dark Web Monitoring
- Quantum Computing Threats
- Secure Coding Practices
- Research Project: Emerging Threats
Capstone & Career Prep
Simulated Enterprise Cyber Defense Project
Resume Building for Cybersecurity Roles
LinkedIn/GitHub Profile Optimization
Mock Interviews (Technical & Behavioral)
Certifications Roadmap (CISSP, OSCP, etc.)
Networking in Cybersecurity Communities
Ethics and Professional Conduct
Final Project: Full-Scale Security Assessment
Master In-Demand Skills with Practical, Industry-Based Learning
What Role Does a Cyber Security Professional Play?
Security Analyst
Monitors and analyzes security incidents to detect threats and protect organizational assets through alerts, reports, and response actions.
Security Engineer
Designs, implements, and maintains security infrastructure like firewalls, intrusion detection systems, and encryption to safeguard networks and systems
Ethical Hacker / Penetration Tester
Simulates cyber-attacks by identifying vulnerabilities and weaknesses in systems to help organizations strengthen their defenses
Incident Response Specialist
Leads investigations into security breaches, contains threats, and develops recovery plans to minimize damage and restore normal operations
Security Architect
Develops and enforces comprehensive security strategies and frameworks aligned with organizational goals and compliance requirements
Cyber Security Consultant
Advises businesses on best practices, risk management, and the latest security technologies to improve overall cyber defense posture
Skills Covered
Threat Analysis
Vulnerability Assessment
Network Security
Ethical Hacking
Incident Response
Security Auditing
Cryptography
SIEM Tools
Cloud Security
Business Intelligence
Cyber Security Tools Covered

Security Analyst
Monitors and analyzes security incidents to detect threats and protect organizational assets through alerts, reports, and response actions.
Security Engineer
Designs, implements, and maintains security infrastructure like firewalls, intrusion detection systems, and encryption to safeguard networks and systems
Ethical Hacker / Penetration Tester
Simulates cyber-attacks by identifying vulnerabilities and weaknesses in systems to help organizations strengthen their defenses
Incident Response Specialist
Leads investigations into security breaches, contains threats, and develops recovery plans to minimize damage and restore normal operations
Security Architect
Develops and enforces comprehensive security strategies and frameworks aligned with organizational goals and compliance requirements
Cyber Security Consultant
Advises businesses on best practices, risk management, and the latest security technologies to improve overall cyber defense posture
Skills Covered
Threat Analysis
Vulnerability Assessment
Network Security
Ethical Hacking
Incident Response
Security Auditing
Cryptography
SIEM Tools
Cloud Security
Business Intelligence
Cyber Security Tools Covered

Career Services


Placement Assistance

Personalized Guidance

Mock Interview Preparation

One-on-One Mentoring session

Career Oriented Seesions

Resume & LinkedIn Profile Building
Career Services


Placement Assistance

Personalized Guidance

Mock Interview Preparation

One-on-One Mentoring session

Career Oriented Seesions

Resume & LinkedIn Profile Building
How our program works
Enhance Your Skills to Transform Your Career Path
- Gain official proof of your expertise from a trusted institution, increasing your value in the eyes of employers and clients.
- Stand out in competitive job markets and unlock better job roles, promotions, or freelance opportunities.
- Certifications ensure your skills are aligned with current industry standards, making you job-ready from day one.
- Completing a certified course strengthens your belief in your capabilities and readiness to tackle real-world challenges.
- Join a professional community, gain access to hiring managers, and receive support from placement partners and mentors.

Cyber Security Projects Covered








Land Your Dream Job Our Alumni






Cyber Security Training FAQs
Can I learn cybersecurity without a technical background?
Answer:
Yes! Many courses cater to beginners, but you’ll need to learn:
Basic networking
Operating systems
Scripting (Python/PowerShell).
Start with foundational courses like Google’s Cybersecurity Certificate or CompTIA Security+.
What tools will I learn in cybersecurity training?
Answer:
You’ll work with tools like:
Nmap (network scanning)
Wireshark (packet analysis)
Metasploit (penetration testing)
Splunk (SIEM)
Burp Suite (web app security).
Is cybersecurity training enough to get a job?
Answer:
Training + certifications + hands-on experience (labs, CTFs, internships) are key. Employers value:
Certifications (e.g., Security+, CEH, CISSP)
Practical skills (e.g., Hack The Box, TryHackMe)
Soft skills (problem-solving, communication)
What’s the difference between ethical hacking and cybersecurity?
Answer:
Cybersecurity: Broad field (defense, risk management, compliance).
Ethical Hacking: Subset focused on offensive security (penetration testing, vulnerability assessments).
Training in both is valuable for roles like Penetration Tester or SOC Analyst.
What’s the best way to practice cybersecurity skills?
Answer:
Hands-on labs: Platforms like TryHackMe, Hack The Box, and CyberSecLabs offer real-world scenarios.
Capture the Flag (CTF) competitions: Develop problem-solving skills (e.g., OverTheWire, picoCTF).
Homelabs: Set up a virtual lab with VirtualBox/Kali Linux to test attacks/defenses.
Is this course available online or offline?
Tech Pragna are offered in both online and offline
What’s the difference between SOC Analyst and Penetration Tester roles?
Answer:
SOC Analyst:
Monitors networks for threats.
Uses SIEM tools (Splunk, Sentinel).
Entry-level friendly.
Penetration Tester:
Proactively hacks systems to find flaws.
Uses Kali Linux, Metasploit.
Requires certifications like OSCP or CEH
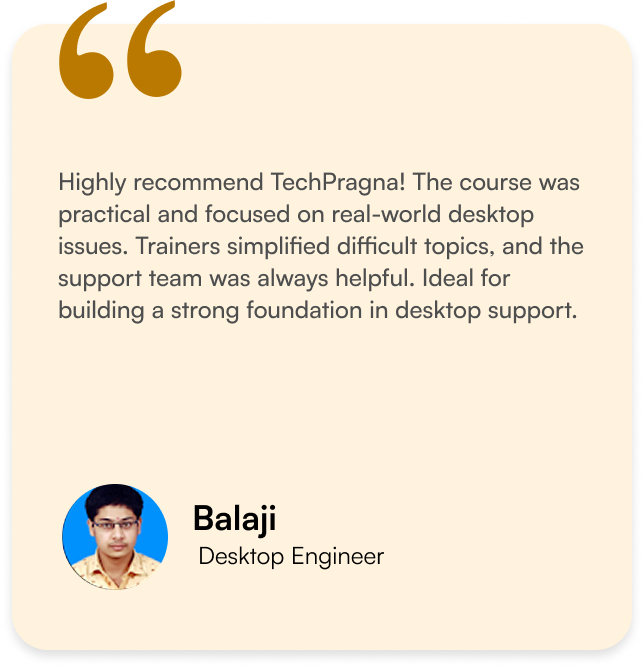
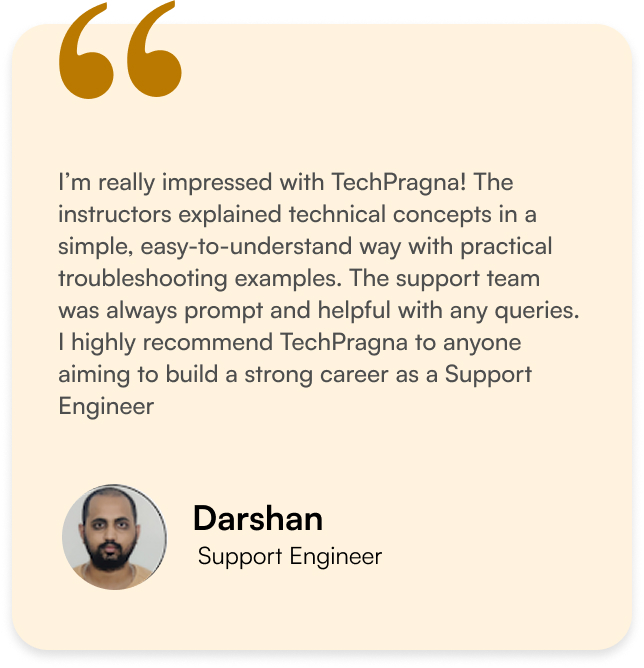
What Our Learners Have To Say






Explore the Latest Trending Courses
Software Testing
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Data Science
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Network Engineering
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Cloud Computing
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Software Testing
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Data Science
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Network Engineering
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study
Cloud Computing
- Online/Offline
- 6 Months
- Professional Level Certification
- Projects and Case Study